IPv6 setup -part 2#
In my previous section, I covered the setup of my ISP connection and Fritz!Box.
This section covers the setup of my firewall and router. (USG)
The USG (Unifi Security Gateway)#
The USG is the most important component in my network. It is the gateway where traffic enters and leaves and in addition to restricting this traffic (firewall), it also manages the internal networking structure and traffic. (routing)
Whilst the USG has it's flaws, in my mind the pros far outweigh the cons.
- home pricepoint
- firewall
- IDS/IPS Intrusion Detection System, Intrusion Protection System (some say marketing hype, but for now I only use the IDS)
- solid router
- web interface for configuration
The configuration is done by a web interface that resides on another device called a
Unifi cloud key Gen 2.. This is used for the central configuration portal for all the Unifi devices in the network, such as switches and WiFi access points.
The USG supports WAN.1, LAN.1, and a third port that can be either WAN.2 or LAN.2.
WAN.1 port is connected to the Fritz!Box.
Internally referred as interface eth0.
LAN.1 port is connected to a network switch for my devices.
Internally referred to as interface eth1.
The firewall is managing the traffic between these two ports.
WAN.2 can be configured if you have a second ISP connection (maybe for backup) or in my case I use LAN.2 for the connection of a Netgear switch.
USG IPv6 routing.#
The first step is configuration of the WAN (Wide Area Network) connection. This is the connection that brings the traffic in to the router from the Internet. I cover how I set this up in the next section, but first I want to show how the interfaces look like for the two main connection types of WAN.
- The first is to make a direct connection from the USG to the ISP using a PPPoE connection (basically a tunnel through the Fritz!Box).
- The second is connecting the WAN port to an upstream router (this is acting like a client of the Fritz!Box).
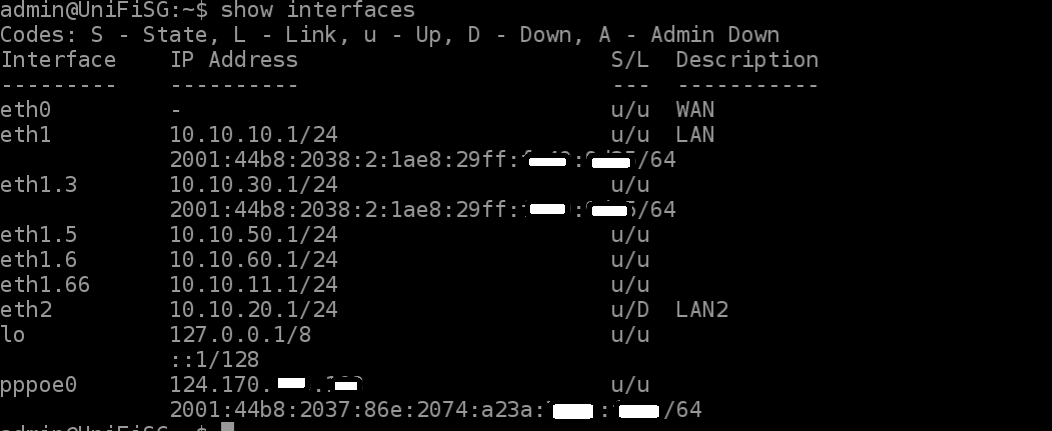
Below shows the result of my original configuration where I was using the PPPoE connection on the WAN port to connect to my ISP.
The pppoe0 interface shows the public dynamic IPs assigned. Received traffic is routed from here to eth1 or eth2. Whilst it worked, it wasn't using the static IPv6 address provided to me.
I also found that there was sometimes a delay (several minutes) in the assignment of the IPv6 public IP from the ISP. This could have been caused by multiple configuration attempts.
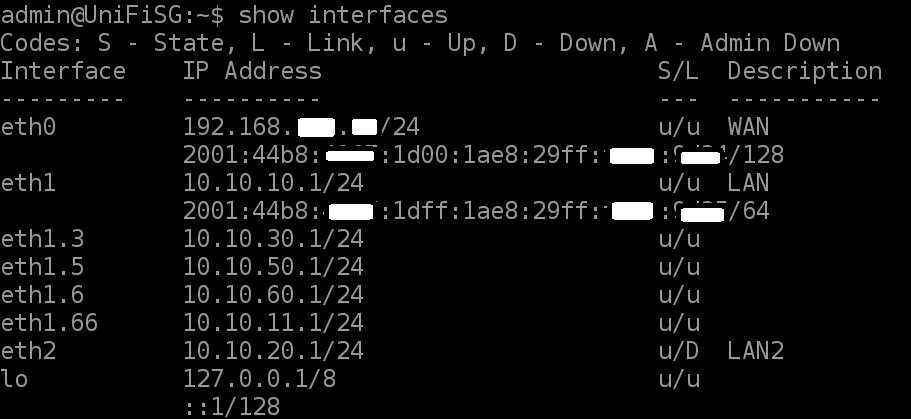
And below shows the final configuration showing the WAN connection to the Fritz!Box.
eth0 (WAN) shows the internal IPv4 address provided by the Fritz!Box and the public IPv6 address.
Static routes#
The IPv6 addresses are routed automatically. IPv6 uses NDP (Neighbor Discovery Protocol) to build up a list of all the device's neighbors and from this it works out the routing paths.
IPv4 requires a static route to be configured so the device knows where to send traffic outside of the current network.
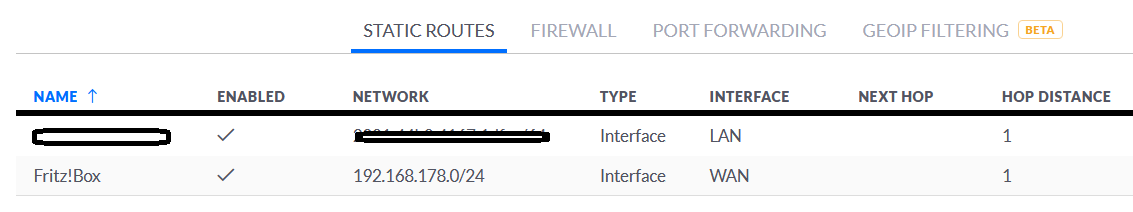
In my case, I have defined 5 static routes on the Fritz!Box, so that it knows where to send traffic for the 10.10.x.x networks. (Ie: send to USG WAN port)
And on the USG I have defined 1 static route, so it knows where to send traffic for 192.168.178.0/24. (Ie: send to Fritz!Box)
USG configuring the WAN#
After a number of configuration variations, it ended up with the few options below.
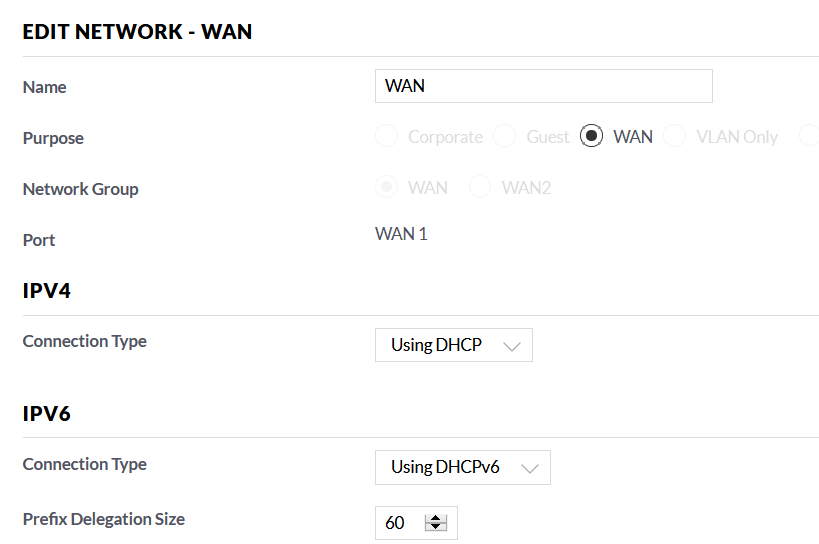
- DHCP to get the IPv4 address. This is fixed in the Fritz!Box.
- And DHCPv6 for the IPv6 address.
I have indicated I wanted a size of /60 from the Fritz!Box. This allows for it to be broken down to 16 smaller networks each of size /64 on the USG.
Issue: I initially assigned a /56 to the WAN port. Whilst this was accepted in the interface, the USG was not able to receive a /56 from the upstream router and hence did not get an IP for it's WAN interface.
IPv6 Delegation size matters.#
The Fritz!Box has been assigned a network size of /56 and needs to keep a part of this for the clients that connect to it.
It can only allocate out a smaller network size /57 through /64.
Issue: The USG wants to assign a /64 to each IPv6 LAN network via the PD attribute field. When you assign the WAN port to request a /64, the LAN networks are not able to subdivide this or assign a /64 for themselves.
I settled with /60 which provides for 16 sub-networks. Each of these subnets themselves can have a huge number of IP addresses for clients.
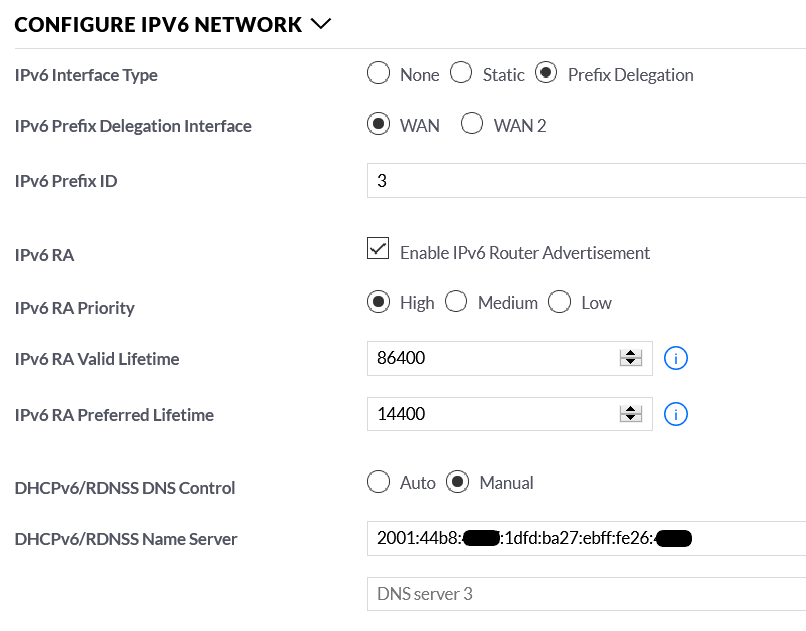
To configure in the USG, I just tell it I want to use PD (Prefix Delegation) mode and provide a Prefix ID which is a number from 0 to f (hexadecimal) ie:6. The USG joins this with the prefix to give you the network.
prefix: 2001:aaaa:bbbb:1d00::/64 Prefix ID: 3 Resulting network: 2001:aaaa:bbbb:1d03::/64
Issue: I faced a problem with the USG web interface in that it wouldn't accept an IPv6 Prefix ID if it had been used on another network. I had previously entered the ID on a network, but then changed the type from PD to a Static. The USG remembered the ID entry although it wasn't used and wasn't shown on the screen.
Assigning your own DNS server.#
I use Pi-hole for my everyday DNS server and for IPv4 this is assigned to my windows10 client via DHCP when I get an IPv4 address.
There is an option to provide the IPv6 address of your DNS server to the network and distribute this using RDNSS (Recursive DNS Server ) for a PD type network. Unfortunately, I found this didn't work for me.
Issue: RDNSS is not recognised by Windows10 clients.
It would only work if I was using DHCPv6 for the network.
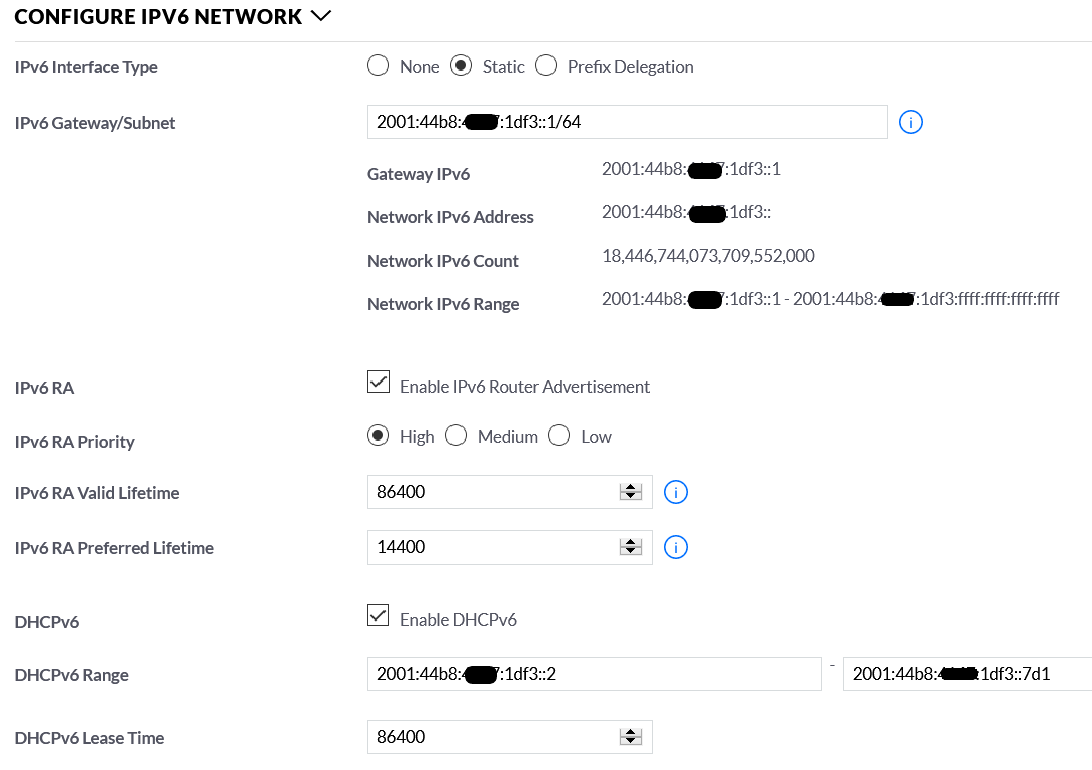
Issue: DHCPv6 is only available if you define a static network. You therefore lose some of the automation benefits of PD type networks.
I used a static network that was within the /60 range and it wasn't difficult to setup and all worked as expected. My client received it's IPv6 address and the IPv6 address of my Pi-hole DNS server.
Which static networks to use#
I first tried to define a static network that was outside of the /60 range allocated to the WAN port on the USG.
I initially didn't want a conflict with the automatically assigned networks from PD.
I assumed that the USG would setup the required routing and firewall rules for this.
It did allow me to define it and also showed this in the show interfaces and also in the show ipv6 routes commands on the USG, but I could not manage to get the client to communicate outside of the network. Ie: traffic was never routed across to the WAN interface. ( I even tried to define static routes, but to no avail.)
Issue: Static networks outside of delegated range to the router did not work.
Firefox browser access to IPv6 only sites#
I mainly Firefox (86) and found that it was preferring IPv4 addresses for accessing web sites.
I encountered an error if a web site used only an IPv6 address. (website not reachable)
Issue: Default behaviour for Firefox is to make a DNS query for the
A recordonly. (ipv4 address). (Observed in network traffic capture)
I found an option in Firefoxabout:configthat altered this behavior to make the DNS query for the IPv6 addressAAAA record.
network.trr.early-AAAA needs to be changed to true
Stocktake - USG#
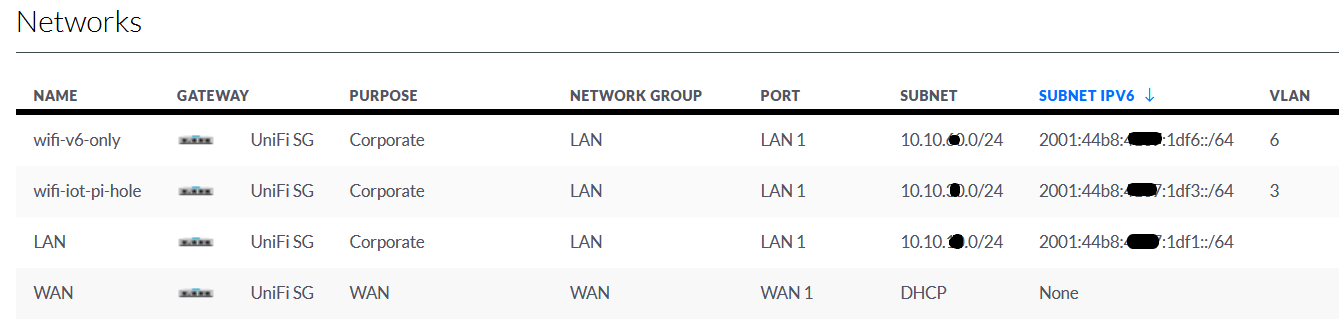
Now we have the USG setup with IPv6. The connected clients can receive their IPv6 address and work with them across the internet. I have several networks setup for different purposes.
In the next section I cover the configuration of my home server, Docker and summarize the issues I faced in my setup.